WHAT IS IT security framework?
As part of the ISO 27000 suite of information security standards, ISO 27001 is a framework that helps organizations “establish, implement, implement, monitor, review, maintain and continuously improve ISMS”.
What are the four tiers of the framework?
Contents
Framework Implementation Piers describes the sophistication of the organization’s cyber security measures based on its risk management process, integrated risk management program, and external involvement in risk management. The four layers are partly risk-based, repeatable and adaptive.
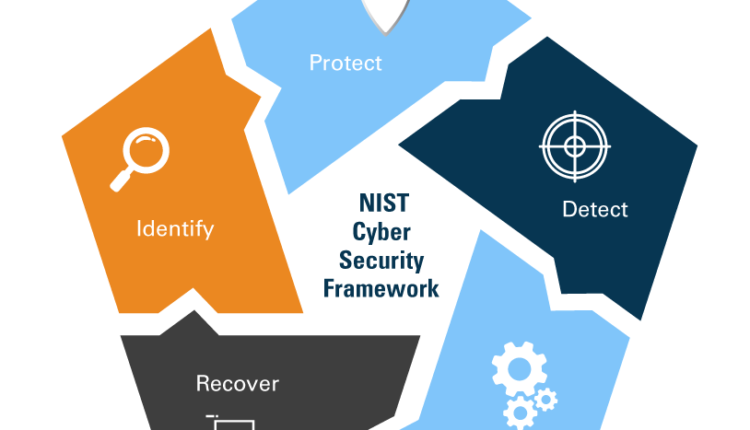
How many categories are there in the NIST Framework? The NIST Cybersecurity Framework organizes its “core” material into five “functions” which are subdivided into a total of 23 “categories”. For each category, it defines a number of cybersecurity result subcategories and security controls, with 108 subcategories in total.
What is the purpose of the NIST Framework tiers?
Organizations using the tiers receive context on their cyber risk and this mechanism enables organizations to understand the features of their cyber security risk management approach that can help them prioritize and achieve their cyber security goals.
What is the purpose of the NIST cybersecurity framework?
NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.
What is meant by Framework implementation tiers?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.
What are the 4 NIST implementation tiers?
These four Tiers are summarized below:
- Tier 1 organizations have ineffective risk management approaches. …
- Tier 2 organizations have informal risk management approaches. …
- Tier 3 organizations have structured risk management approaches. …
- Tier 4 organizations have adaptive risk management approaches.
What are the NIST CSF tiers?
These four Tiers are summarized below:
- Tier 1 organizations have ineffective risk management approaches. …
- Security Compliance Management and Audit An information security compliance management program includes a minimum set of data protection security requirements that apply to any organization that stores, processes, or transmits that data.
- In cyber security, compliance means creating a program that establishes risk-based controls to protect the integrity, confidentiality and accessibility of information stored, processed or transmitted.
- The 140 series of Federal Information Processing Standards (FIPS) are U.S. government computer security standards that specify requirements for cryptography modules.
What are the 5 NIST CSF categories?
ISO / IEC 27001 is used worldwide as a yardstick for effective information security management. This is the only universally recognized certification standard for information and cyber security. This standard is the latest version of the world’s leading standard for the specification of information security controls.
What are Framework implementation tiers?
ISO / IEC 27001 provides a framework for companies to manage their data security. Establishes requirements for information security controls that control people, processes and technology and protect valuable company data.
What are the 5 NIST CSF categories?
These requirements are across the three leadership obligations under which the ten data security standards are grouped: people, process and technology.
What are the 3 key ingredients in a security framework?
Cyber Security Standards
What are the security standards?
ISO 27001. This is one of the common standards that the organization adheres to operating an information security management system. …
PCI DSS. PCI DSS stands for Payment Card Industry Data Security Standard. …
What are security compliance standards?
HIPAA. HIPAA stands for the Health Insurance Portability and Liability Act. …
What is security compliance management?
FINRA. …
What is network security compliance?
GDPR.
How many information security standards are there?
PCI DSS s’applique aux qué traitent des cartes de paiement, ko sotteu prea, acqu prete pre pre pre pre pre pre pre pre services services services services services services services services services plus plus plus plus plus plus plus plus plus plus plus plus plus plus plus, qu qu,,,,,,,,,,,,,,,,,,,,, it cart cart trans «« «« «« «« «« «« «« «« «« «« «« «cart« «« «« cart cart «cart cart« «« «« «« cart cart cart cart cart cart cart cart «cart« cart «cart« cart «cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart cart.
What are the IT security standards?
The five domains in the NIST framework are the pillars that support the creation of a successful and holistic cyber security plan. They include identification, protection, detection, response and recovery.
What are the ISO standards for information security?
The NIST Cybersecurity Framework, NIST 800-53 and NIST 171. Although these three frameworks share most elements in common, there are some minor differences in structure and controls based on their specific use cases.
How many data security standards are there?
An IT security framework is a documented set of processes used to define policies and procedures around the ongoing implementation and management of information security controls in an enterprise environment. … Developed some industry-specific frameworks, as well as various regulatory compliance goals.
What kind of security standards are available?
What is a security management framework? The Safe Controls Framework (SCF) is a comprehensive catalog of controls designed to enable companies to design, build and maintain secure processes, systems and applications.
- A framework allows standardization of service delivery that improves efficiency and profitability. Many organizations operate frameworks to establish a common language among themselves and their clients. For example, frameworks allow you to align conversations with customers on what they want â € œgoodâ € to look like.
- The Cybersecurity Framework consists of three main components: the Core, Implementation Tiers, and Profiles. The Framework Core provides a set of desirable cyber security activities and outcomes using a common language that is easy to understand.
- These functions are: identity, protection, detection, response and enhancement. They support an organization in articulating its management of cyber security risk by addressing threats and developing through learning from past activities.
- A security framework is a collection of international cyber security policies and processes mandated by the state to protect critical infrastructure. It contains detailed instructions for companies to handle the personal information stored in systems to reduce their exposure to security-related risks.
- Organizations using the tiers receive context on their cyber risk and this mechanism enables organizations to understand the features of their cyber security risk management approach that can help them prioritize and achieve their cyber security goals.4
Où s’applique la norme PCI DSS ?
Organizations using the tiers receive context on their cyber risk and this mechanism enables organizations to understand the features of their cyber security risk management approach that can help them prioritize and achieve their cyber security goals.5
Qui doit être certifié PCI DSS ?
Organizations using the tiers receive context on their cyber risk and this mechanism enables organizations to understand the features of their cyber security risk management approach that can help them prioritize and achieve their cyber security goals.6
Quelles sont les données concernées par PCI DSS ?
Organizations using the tiers receive context on their cyber risk and this mechanism enables organizations to understand the features of their cyber security risk management approach that can help them prioritize and achieve their cyber security goals.7
What is framework cybersecurity?
Organizations using the tiers receive context on their cyber risk and this mechanism enables organizations to understand the features of their cyber security risk management approach that can help them prioritize and achieve their cyber security goals.8
Organizations using the tiers receive context on their cyber risk and this mechanism enables organizations to understand the features of their cyber security risk management approach that can help them prioritize and achieve their cyber security goals.9
- NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.0
- NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.1
- NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.2
- NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.3
- NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.4
Why is cybersecurity framework important?
NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.5
Why is the NIST Cybersecurity Framework important?
NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.6
Why was cybersecurity framework created?
NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.7
Which cybersecurity framework function is the most important?
NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.8
What is a framework in cybersecurity?
NIST is the National Institute of Standards and Technology in the US Department of Commerce. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage and reduce their cybersecurity risk and protect their networks and data. The Framework is voluntary.9
What is cyber security framework?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.0
Why is cyber security framework important?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.1
What are the different types of cybersecurity frameworks?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.2
What are the 5 cybersecurity domains?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.3
What are the different NIST frameworks?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.4
What are IT security frameworks?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.5
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.6
Why are security frameworks necessary?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.7
What are the 3 key ingredients in a security framework?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.8
What are the three parts of the NIST cybersecurity framework?
Framework Implementation Tiers Layers describe the extent to which an organization’s cyber security risk management practices demonstrate the features defined in the Framework.9
What is a security framework?
These four Tiers are summarized below:0

Comments are closed.