WHAT IS IT security concept?
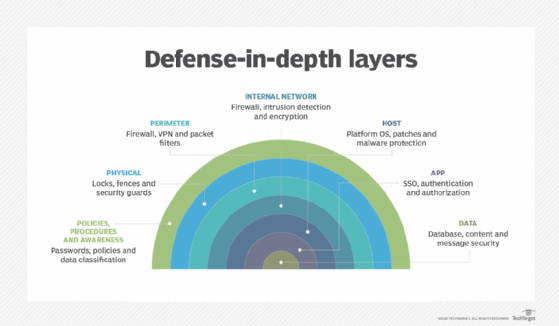
What are the 7 layers of security?
Contents
The seven layers of the OSI model are: the human layer, the perimeter layer, the network layer, the endpoint layer, the application layer, the data layer, and the mission-critical layer.
What are the elements of layered protection? Layered protection, as in the previous example, is known as deep protection. This security is implemented in overlapping layers that provide the three components needed to safeguard resources: prevention, detection, and response.
What are the different layers of security?
What are the 5 layers of security?
- Active attacks. When an active attack occurs, the perpetrator often tries to exploit any vulnerabilities to gain access to and control the network. …
- Passive attacks. …
- Protection of solution boundaries. …
- Network security. …
- Endpoint security. …
- Data protection. …
- Security Awareness Training.
What is security and its layers?
Layered security refers to security systems that use multiple components to protect operations on multiple levels or layers. … The purpose of a multi-layered approach to security is to ensure that every single element of your cybersecurity plan is backed up to counter any errors or vulnerabilities.
How many layers are there in security?
Seven layers of cybersecurity.
How many security layers are there?
What are the 7 layers of security? This question is a bit more complex than it sounds. Many readers may be familiar with the OSI model, a framework used by many early cybersecurity users to prescribe security solutions related to a network system.
How many layers are there in security?
Seven layers of cybersecurity.
What are the layers of security in cyber security?
To protect your business or organization from a cyberattack, follow the 5 main technical controls listed below, each of which we’ll cover in more detail: Firewalls. Safe configuration. User access control.
What are the three types of security?
There are three main areas or classifications of security control. These include management security, operational security, and physical security controls.
What is information security and assurance?
Provision and security of information is the management and protection of knowledge, information and data. It combines two areas: Information Provision, which focuses on ensuring the availability, integrity, authentication, confidentiality and non-repudiation of information and systems.
Why is information important? An IA is important to organizations as it ensures that user data is protected both in transit and during storage. Information provision has become an important component of data security as transactions and business processes consistently rely on digital handling practices.
What are the principles of security testing?
While the three characteristics above represent basic security principles, the six basic concepts in security testing are:
- confidentiality;
- integrity;
- authentication;
- availability;
- authorization;
- non-repudiation;
What are the basic safety rules? The basic principles (principles) of information security are confidentiality, integrity and availability. Each element of an information security program (and each security review implemented by an entity) should be designed to achieve one or more of these principles. Together they call themselves the CIA Triad.
Which of the principles needs to be verified by security testing?
Security testing is a process aimed at revealing gaps in information system security mechanisms that protect data and maintain functionality as intended. … Typical security requirements may include certain elements of confidentiality, integrity, authentication, availability, authorization and non-repudiation.
Which principle of security testing means that data should not be changed?
Integrity: This includes maintaining data consistency, accuracy and reliability throughout its lifecycle, and enables accurate and desired information to be transmitted from senders to intended recipients. It ensures that data cannot be changed by unauthorized persons (for example, in breach of confidentiality).

Comments are closed.