What companies have had ransomware attacks?
Has Apple been hacked recently?
Contents
Apple’s latest disaster occurred in September 2021, when researchers discovered that Israeli spyware had infected iOS devices with a click of zero.
Who stole Apple recently? Chinese critics who took part in the annual Tianfu Cup in Chengdu, China have reportedly been able to break the security of the latest iPhones, the iPhone 13 Pro, running iOS 15.0. 2 software per second.
What does it mean when Apple says this password has appeared in a data leak?
According to Apple, your iPhone or iPad constantly checks the passwords you have stored in the AutoFill keychain password against a list of passwords that have come to light. … It only indicates that your password was generated by a data leak, and therefore, your account is at risk.
What is Apple data leak?
When users uninstalled infected apps from the App Store, their devices crashed. The violation affected 128 million iPhone users, including 18 million in the United States. At the time, Apple did not disclose the extent of the offense to the affected iPhone users.
Can iphones detect if your passwords been leaked?
Although Apple’s security check will alert you if your account appears in a known data area, your iPhone or iPad may not notify you until you use a key to sign in.
Should I change my password if it was in a data leak?
If your password is damaged, you must change it not only to a broken service but also wherever you used that password. The quickest way to do this is to use a password manager, which allows you to store unique, complex passwords for each account.
Is Apple getting hacked 2021?
They discovered my weaknesses (and, perhaps, previously used) by government agents of the NSO group, Israel company Spyware, to defraud iPhones and other Apple devices from January 2021.
Who hacked Apple 2021?
REvil first tried to destroy Quanta for $ 50M for not making the files available to the public, and later tried something similar with Apple. When this failed, REvil went ahead and released plans that unveiled new ports available for the 2021 MacBook Pro.
Can an iPhone camera be hacked 2021?
The iPhone is undoubtedly more competitive than it is when it comes to demolition. … Well, like anything else running software, your iPhone does not have 100 percent hack-proof. There have been cases when the user iDevice has been compromised. So, yes, your iPhone can be hacked.
Who hacked Apple 2021?
REvil first tried to destroy Quanta for $ 50M for not making the files available to the public, and later tried something similar with Apple. When this failed, REvil went ahead and released plans that unveiled new ports available for the 2021 MacBook Pro.
Did Apple get hacked?
Apple fixes a security error that was used to hack some of its products, including the iPhone. Apple has released an important software patch to fix security that some researchers may allow criminals to infect iPhones and other Apple devices directly without user interaction.
What is a famous ransomware attack?
WannaCry ransomware attack became a global cyberattack in May 2017 by WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by deleting data and demanding cryptocurrency payments of Bitcoin.
What is a well-known example of ransomware? A notable example of the ransomware attack that hit companies worldwide was the 2017 WannaCry explosion, which affected more than 200,000 computers in more than 150 countries.
What was the first ransomware attack?
One of the first ransom attacks ever recorded was the AIDS trojan (PC Cyborg Virus) which was released on a floppy disk in 1989. The victims had to send $ 189 to P.O. a Panamanian box to regain access to their systems, though it was a simple virus that used symmetric cryptography.
How was the ransomware attack initiated?
Ransomware is usually transmitted through phishing emails with malicious links or downloads. Auto-download occurs when a user visits an infected website unknowingly, and the malware is downloaded and installed without the user’s knowledge.
When was the first ransomware attack?
Since 1989 with the first reported release known as the AIDS trojan, the use of ransomware has increased dramatically internationally. There were 181.5 million ransom attacks in the first six months of 2018.
What is a real world example of a ransomware attack?
The incident began in May 2017, when criminals infected a computer with WannaCry ransomware. In one day, more than 230,000 computer users around the world discovered that their files were encrypted – and that they could only access their data by paying Bitcoin to attackers.
What is an example of ransomware attack?
A notable example of the ransomware attack that hit companies worldwide was the 2017 WannaCry explosion, which affected more than 200,000 computers in more than 150 countries. It cost the UK £ 92 million and to cover global costs up to £ 6 billion.
What is an example of ransomware?
Advanced examples of redemption. Cryptolocker is one of the redemption models that Comodo has targeted. … Cryptolocker is known for encrypting user files and requires payment later to open it. Comodo creates a hard drive shadow type to immediately protect important files from cryptolocker.
What are the most common ransomware attacks?
Phishing rose to # 1 in Q4 of 2020 as the most widely used vector of redemption. Using links, links, or both, the phishing email scam seeks to trick users into taking action. Phishing emails with links may appear to be from a reputable person asking a user to submit credentials for a false purpose.
What is an example of ransomware?
Advanced examples of redemption. Cryptolocker is one of the redemption models that Comodo has targeted. … Cryptolocker is known for encrypting user files and requires payment later to open it. Comodo creates a hard drive shadow type to immediately protect important files from cryptolocker.
Is WannaCry an example of ransomware?
WannaCry is an example of crypto ransomware, a type of malware that is used by cybercriminals to defraud money. Ransomware does this by paying for important files, so you can’t read them, or lock them out of your computer, so you can’t use it.
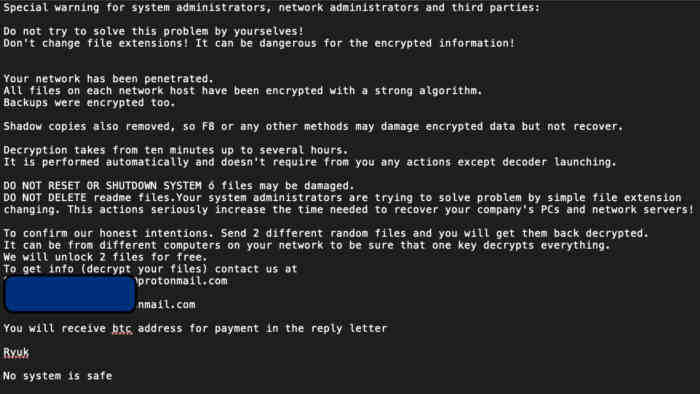
What is the most common ransomware?
The 10 most popular types of ransom
- GoldenEye.
- Jigsaw.
- Locky.
- Maze.
- It’s still Petya.
- Petya.
- Ryuk.
- Wannacry.
What type of virus is ransomware?
Ransomware is a type of malware from cryptovirology that threatens to disclose the victim’s information or permanently prevents access to it unless a ransom is paid.
How many data breaches have there been in 2021?
Also, the number of crimes they recorded in 2021 has exceeded the total number of FY-Year 2020 incidents by 17%, with 1,291 offenses in 2021 compared to 1,108 offenses by 2020.
How many data breaches occurred in 2021? However, the number of crimes up to 30 September 2021 has increased the total number of incidents for the full year 2020 by 17 percent (1,291 offenses by 2021 compared to 1,108 offenses by 2020).
Who has been hacked in 2021?
2021 Big Data Data Disorders – To date
- Colonial Pipeline. Paid Redeem: $ 2.3 million in Bitcoin. …
- Facebook, Instagram and LinkedIn through Socialarks. Broken records: 214 million …
- Bonobos. Broken records: 7 million. …
- Kroger’s Accellion. …
- Parler. …
- Volkswagen and Audi. …
- Destroy Your Data Quality with PCI P2PE and ShieldConex®
Is the Trojan virus real?
Trojans can affect cellular devices as well as desktop computers and laptops. Both Android and iOS are affected by Trojan horse malware, although Android trojans are very common.
Is the Trojan virus illegal? Trojan horses are copied onto computers by a computer owner and, like Greek soldiers sneaking up on Troy, there is a secret program installed on the computer. … Making and distributing trojan horse computer software is illegal, such as botnet control and computer use for malicious purposes.
Is the Trojan phone virus real?
Generally, Trojan will attach what looks like an acceptable program. In fact, it is a fake type of app, installed with malware. … Another type of Trojan malware is targeted at Android devices in particular. Called Switcher Trojan, it infects users’ devices to attack routers on their wireless network.
Is there a Trojan virus on iPhone?
There are no Trojan Horses or known viruses that can affect non-prison iPhones. And there are no trash cans on your iPhone.
Is the virus warning on my phone real?
Is the Google virus warning true? Che. When Google says you have a virus on your phone, you are being scammed. In particular, criminals try to trick you into installing malware, providing your personal information, or paying for viruses.
Is Trojan phone virus real?
Generally, Trojan will attach what looks like an acceptable program. In fact, it is a fake type of app, installed with malware. … Another type of Trojan malware is targeted at Android devices in particular.
How bad is a Trojan virus?
Trojan can have one or more destructive usesâ € ”which is what makes them malicious. It is also important to note that unlike viruses, Trojans does not reproduce and spread only by accidentally downloading users, usually from an email link or by visiting an infected site.
Is a Trojan worse than a virus?
Trojan horse is not a virus. It is a destructive program that looks like a real use. Unlike viruses, Trojan horses do not reproduce but can do so.
What does a Trojan virus do?
Another type of Trojan malware is targeted at Android devices in particular. Called Switcher Trojan, it infects users’ devices to attack routers on their wireless network. The result? Cybercriminals can direct traffic to Wi-Fi hotspots and use them to commit various crimes.
Should I worry about a Trojan virus?
Disruption: It can disrupt the entire computer system. It is a crime: without damaging your property (or your business), it can also be harmful to you personally: trojans can steal your information. Tolerant: It cannot always be removed by antivirus programs.

Comments are closed.